Perfect Tips About How To Detect Confliker

Felix and i had a discussion with dan kaminsky about the.
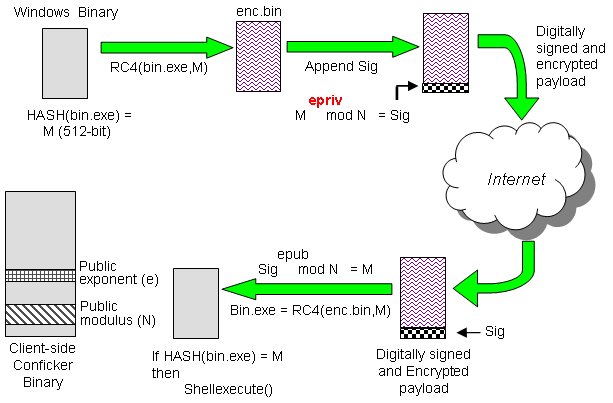
How to detect confliker. However, there is a free, easy way to detect and remove it: Checking for conficker.c or higher. Malware like zeus, conficker and many others use dgas (domain generation algorithms) to build resilient c2 servers.
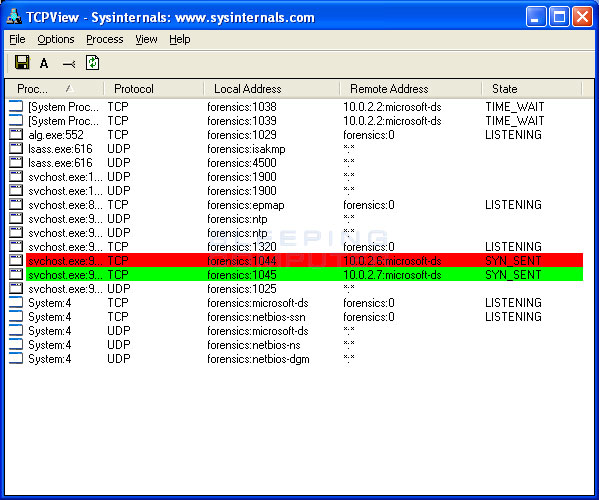
The latest version of nmap has the ability to detect all (current) variants of conficker by detecting the otherwise almost invisible changes that the worm makes to the port 139 and port 445. | check 1 (port 44329/tcp): Run the malicious software removal tool.
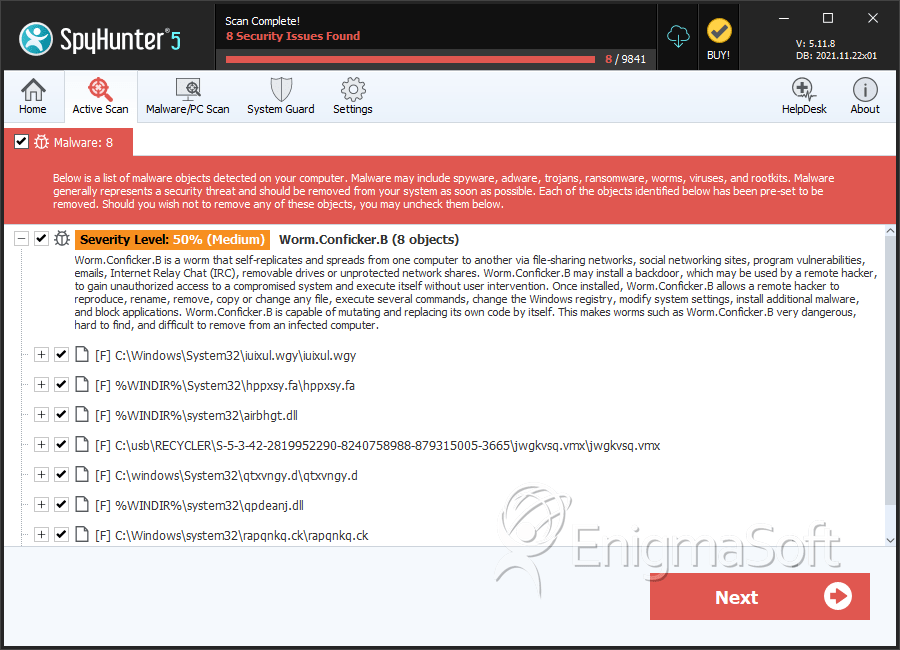
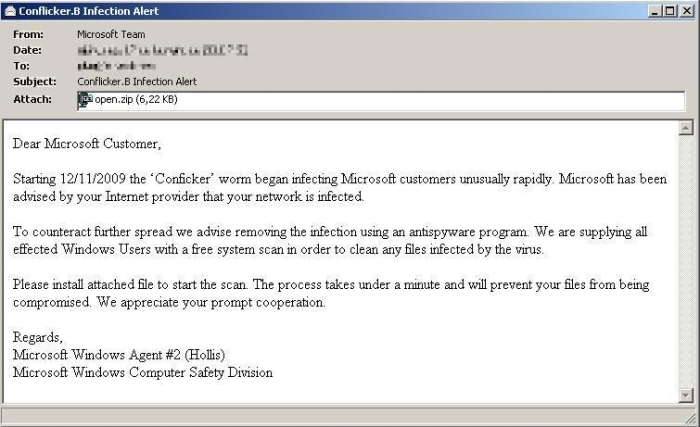
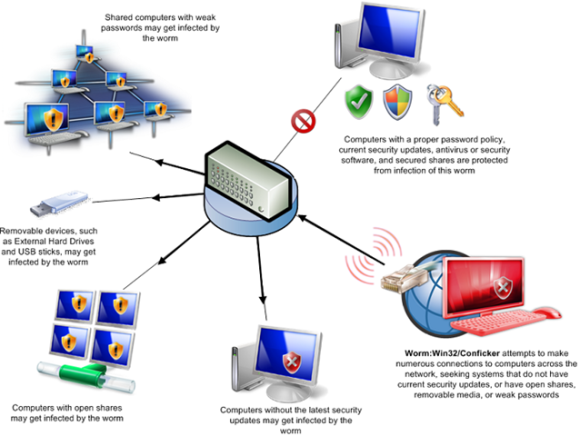
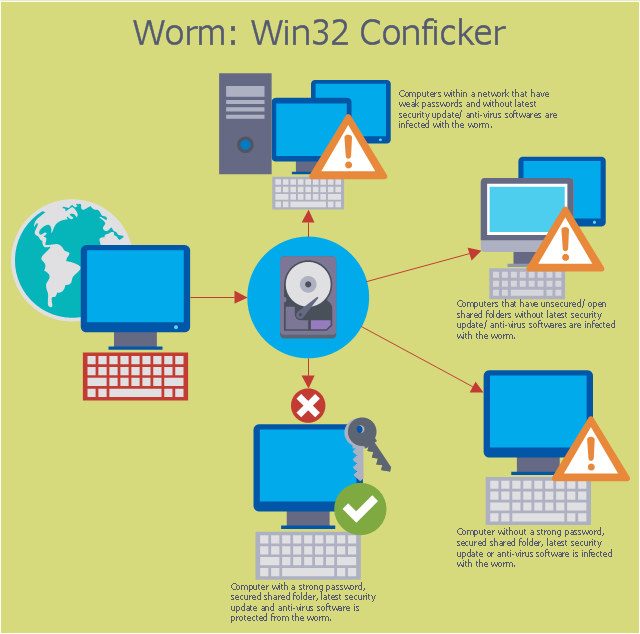
If you choose not to. Details of some variants detected and removed by sav are listed below. Conficker, also known as downup, downadup and kido, is a computer worm targeting the microsoft windows operating system that was first detected in november 2008.
(opens in new tab) from the microsoft malware protection center. How to detect conficker a. Brief overview of the conficker worm and how the languardian can be used to detect its presence
Check the threat logs for any.